Spear Phishing: A Personal Tale
This article includes explicit language and describes a crime with sexual overtones.
A Targeted Phishing Attack: One Woman's Harrowing Experience
The digital age has brought countless conveniences, but also new dangers lurking behind familiar interfaces. One Reddit user's experience highlights the sophisticated evolution of online scams that prey on trust and personal connections.
Unlike traditional phishing attempts that cast wide nets hoping for random victims, this case exemplifies a targeted attack known as spear phishing—a method that focuses on specific individuals using personalized information to appear legitimate.
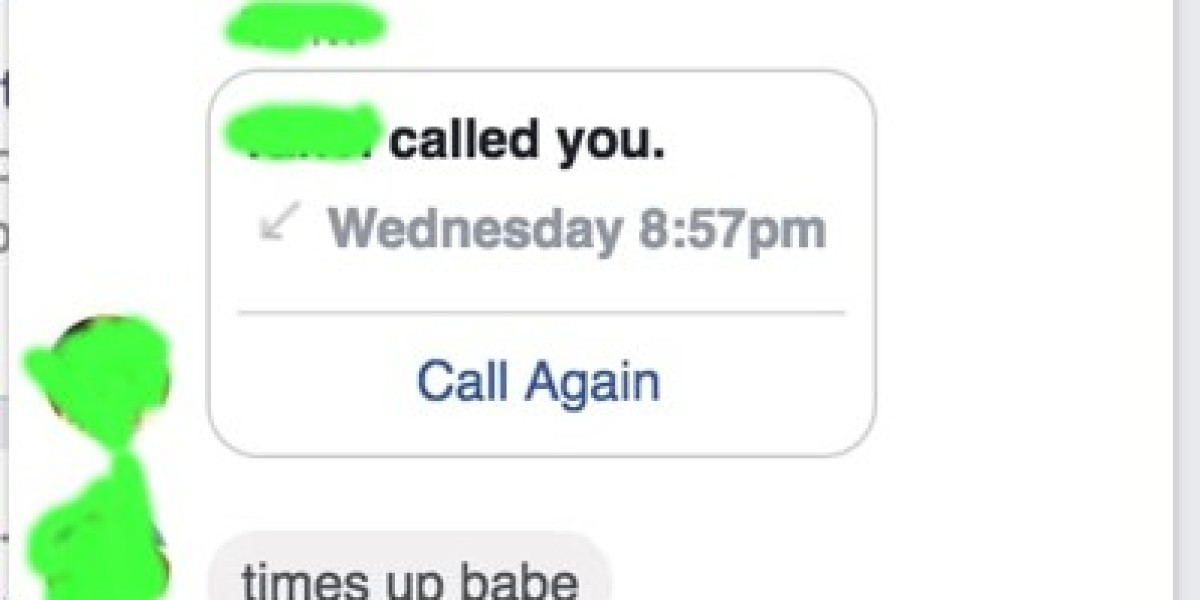
The incident began innocently enough with what appeared to be a simple request from a known contact on Facebook. The victim was asked to participate in an online modeling competition, requiring her to share her Apple and Google credentials to join a group. When a supposed technical issue arose, she was asked for her password to resolve it.
This moment of trust became the turning point in a rapidly unfolding nightmare.
Within minutes of sharing her credentials, the victim received notifications of logins from Pakistan. The attacker moved with alarming efficiency, locking her out of her accounts by changing recovery information, security questions, and contact details. Without two-factor authentication in place, there were few barriers to the attacker's progress.
The situation escalated from account theft to blackmail when the perpetrator made contact through the victim's boyfriend. Rather than demanding money, the attacker threatened to publish private photos from her iCloud account on her Facebook profile unless certain demands were met.
When she refused to comply, the attacker carried out the threat. Fortunately, a quick-acting support network of friends was ready to flag and report the content.
Security experts note that spear phishing has become alarmingly effective in corporate environments, with studies indicating that 95% of successful enterprise network breaches begin with such targeted deception. A separate survey found that 91% of respondents had encountered these personalized attacks.
Though typically aimed at executives or IT administrators with access to sensitive systems, this case demonstrates that ordinary individuals can also become targets of these sophisticated schemes.
The victim chose to share her experience publicly, hoping that awareness might prevent others from falling into similar traps. Her story serves as a powerful reminder of the importance of digital security measures like two-factor authentication and the need for vigilance even when interacting with seemingly familiar contacts online.
Cybersecurity Consequences
In a matter of minutes, her social media presence vanished, but the consequences lingered far beyond that brief window.
Over the following four weeks, she meticulously worked to restore her digital identity piece by piece.
The cybercriminal had exploited her compromised account to contact approximately two dozen women in her friend circle. Unfortunately, one friend fell victim to the same scheme, suffering complete account takeover. In an unexpected turn, the perpetrator even attempted voice communication with this second victim, resulting in a heated verbal confrontation with her partner that apparently ended the harassment campaign.
Cybercrime Realities and Solutions
Cybercrime units often dismiss individual cases as low-priority
even when lives unravel through digital extortion
Zed discovered this harsh reality after authorities shrugged off her transnational hacking nightmare
While big tech firms like Apple and Google swiftly helped reclaim hijacked accounts
others left users stranded in security limbo
The disparity in corporate responsibility became glaringly obvious during her recovery efforts
Personalized cyberattacks thrive in shadows of silence
Zed broke this cycle by publicly detailing her trauma
transforming victimhood into a masterclass in digital self-defense
Reused credentials became her Achilles' heel
Now she advocates treating passwords like biometric data – never shared
even through seemingly secure channels
Password managers emerged as non-negotiable armor
though their adoption requires cautious research
The real game-changer? Layered authentication protocols
Physical security keys and authenticator apps now guard her digital gates
rendering SMS codes obsolete relics in her defense strategy
Corporate executives should heed her hard-won insights
Malware-free breaches through psychological manipulation
prove human firewalls need constant reinforcement
Hyperlink hygiene became her new obsession
URL forensics through cursor hovering
and distrust of sleek subdomains now prevent landing on fraudulent clones
As ransomware gangs refine their tactics
Zed's saga exposes systemic failures
from apathetic law enforcement to inconsistent corporate safeguards
Her story isn't about rare misfortune
but the standard playbook for modern digital predators
What is a Netflix VPN and How to Get One
A Netflix VPN is a specialized tool that enables viewers to bypass geographical restrictions on streaming content, allowing access to shows and movies that might be exclusively available in other countries. By masking your actual location and routing your connection through servers in different regions, a Netflix VPN effectively tricks the platform into thinking you're browsing from wherever the server is located, unlocking a vastly expanded library of entertainment options that would otherwise be inaccessible.
Why Choose SafeShell as Your Netflix VPN?
If you’re looking to access region-restricted Netflix content seamlessly, SafeShell VPN is an excellent choice for keeping your streaming experience Netflix unblocked and hassle-free. Here’s why:
- High-speed streaming : SafeShell VPN offers servers optimized explicitly for Netflix, ensuring smooth playback in HD without lags or buffering.
- Multi-device compatibility : Connect up to five devices at once across platforms like Windows, macOS, iOS, Android, and smart TVs, so everyone in your household can stream their favorite shows.
- Exclusive App Mode : Unlock libraries from multiple regions simultaneously, letting you explore global content without switching servers manually.
- Unmatched speed and reliability : With no bandwidth limits, enjoy lightning-fast connections for streaming, downloads, and browsing.
- Advanced security : The proprietary "ShellGuard" protocol encrypts your data, protecting your privacy while you stream or browse.
- Risk-free trial : Test all features with a flexible free trial, experiencing high-speed Netflix unblocked access and top-tier security before committing. SafeShell VPN combines performance, versatility, and peace of mind for your streaming needs.
A Step-by-Step Guide to Watch Netflix with SafeShell VPN
To start using SafeShell Netflix VPN , the first step is to subscribe to the service. Visit the official SafeShell VPN website and select a plan that suits your needs and budget. Once you have chosen your plan, click the "Subscribe Now" button to complete the subscription process.
Next, download and install the SafeShell VPN app on your device. Go to the SafeShell VPN website and select the appropriate version for your device, whether it's Windows, macOS, iOS, or Android. After downloading, install the app and launch it. Log in to your account by clicking on the "Log In" button. SafeShell offers two modes, but for the best Netflix experience, it is recommended to choose the APP mode.
Finally, choose a server from the list of available options. Select a server located in the region whose Netflix content you want to access, such as the US, UK, or Canada. Click on "Connect" to establish the connection. Once connected, open the Netflix app or visit the Netflix website, log in with your Netflix account, and enjoy streaming the content available in the selected region.